Phishing is the practice of sending fraudulent communications that appear to come from a legitimate and reputable source, usually through email and text messaging, for the purpose of tricking those targeted into revealing personal or confidential information which can then be used illicitly.
If you've been phished:
Call ITAC immediately for assistance in resetting your password and limiting any potential damage. Report any possible phishing emails using the "Report Phishing" button in Outlook for Windows or Office 365, or you can forward any phishing or suspicious emails you received in your TXST email as an attachment to abuse@txstate.edu.
About the ISO Phishing Guide
This guide is intended to provide some instruction on how to protect yourself from getting phished or scammed and provide educational resources on cybersecurity. It primarily covers the big three types of social engineering: email phishing, text smishing, and phone vishing via VoIP (Voice of IP).
Any of the threats discussed in this guide can manifest “in the wild” in a number of ways, and are often interrelated to the type of phishing they use. This guide is not intended to be comprehensive and end users should critically evaluate everything they see or read on the internet.
Identifying Phishing
Phishing succeeds if a victim believes the lie that a phisher or scammer is spinning in their communications. A number of tactics can be employed but they all revolve around some basic human psychology which can be exploited by an attacker to gain the trust and confidence of a victim long enough to get what they want.
Knowing how to identify phishing messages, and the appropriate ways to respond, will go a long way towards protecting yourself. Once you can spot phishing messages you will be less likely to fall for even the most convincing ones. Take a few minutes to inspect the image below to get a feel for what you should be on the lookout for and why.
Goals of Phishing
Phishing, generally speaking, is out to steal something. This could be a set of credentials (username and password), Personally Identifiable Information (PII), money, banking or other financial information, unpublished research or other sensitive research data, the list goes on.
The ways that phishing execute on the above listed goals and outcomes can vary from simple social engineering – such as an email pretending to be your boss sent from a random Gmail account trying to get you to purchase them gift cards – to complex spearphishing that leads ransomware attacks and large scale security incidents.
Common Scams
Some common phishing strategies are explained in the list below. This is not an exhaustive list, but these are common phishing scams and strategies that you might encounter “in the wild.”
- Money Mule - a money mule scam often begins with a fake job offer that is too good to be true, or promises quick money for easy work. A victim will receive an mail form someone claiming to be affiliated with the university or major organization, often including some verifiable contact information in the email to throw off a victim's sense of scrutiny.
Scammers first try to get victims to engage with email accounts other than their university account, since there is less security on a personal email account than an enterprise email account like the TXST university email system. Since these are framed as job opportunities, people are asked to give over their most sensitive personal information which can be used for exploitation or identity theft
Scammers will sometimes send a check as an “advance” for the work that is beyond the promised amount with the additional instruction that the difference between what was offered originally and the amount of the actual check be sent back to the sender. Often this can be hundreds of dollars and puts the victim in the position of cashing a fraudulent check, a potential federal felony.
- Gift Card scam - this is a less complex and involved scam than a money mule, but a similar strategy is at play. A scammer will use a fraudulent personal email account that looks like it belongs to a staff supervisor in order to email a staff member or student worker and request that the would-be victim to purchase a number of gift cards.
The scammer tells the victim that they will be reimbursed from the supervisors personal funds. Then, the scammer tells the victim to send pictures of the gift card numbers to the intended “recipient” of the “gift”. Once those gift cards are sent to the scammer there is no way to get funds returned to the victim.
- IRS or “Authority” Scam - A very common scam during tax season. A victim will receive a phone call from someone claiming to be from the IRS and that the victim has unpaid taxes that need to be resolved or they will face arrest and prosecution. The caller will try to coerce the victim into sending money via gift card or other electronic funds.
A variation of this is the Sheriff's office calling, or the local police, calling to say that the potential victim faces arrest over unpaid tickets, fines, or other legal costs. The thing to remember is that the IRS won't call you out of the blue, neither will your local police or Sheriff's, unless you have previously contacted them and have a reasonable cause to believe they would be contacting you. These kinds of communications don't occur unprompted, though, and will never be accompanied by threats or coercion.
Example Phishing Email
This email was received by students during the normal tuition refund processing period during a fall semester. The senders took time to identify valid entities like “CatsWeb” and the “studentinfo.txstate.edu” URL format.
The social engineering tactics used in this phishing email include appeals to authority (Bursar's Office) and urgency (“To be safe, please check now”), both common tactics in social engineering and phishing.
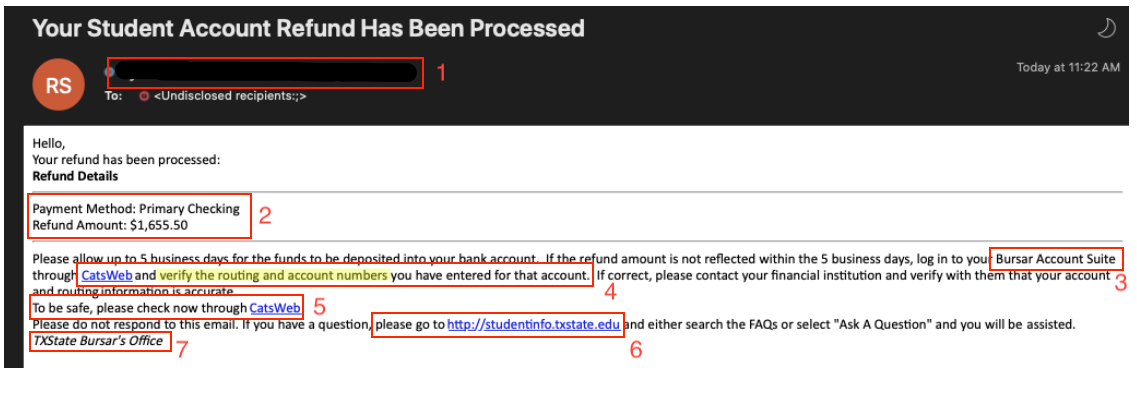
Breakdown of email:
- Redacted email of a compromised .edu account - this was an individual's user account from another education institution that had been used to send out these phishing emails. Since .edu accounts are given a high degree of implicit trust, they are frequent targets of scammers and phishers. However, almost all business conducted by office in the university uses a shared or office email address, it would be very unusual to receive a personal email from someone in the Financial Aid Office, so this should immediately be a huge red flag.
- Specific information that can be confirmed or denied: the phisher has used specificity as a tactic here to try and increase perceived legitimacy of the phishing email. However, this information is verifiable and can be compared against legitimate records of education loan refunds in your student business portal.
- Non-existent application: the phrase “Bursar Account Suite” is nonsensical in context of Texas State University's financial aid process. Since all transactions go through the Financial Aid Office, and all communications come from them, this should also be a red flag.
- Suspicious call to action - “verification”: Always be aware of unsolicited emails that ask you to verify information. Most verification emails come immediately after you have done something; set up an account, changed an account setting, logged in from a new device, etc. The Financial Aid Office will never ask you to verify banking information via email in this manner, nor would most reputable companies.
- Suspicious call to action and emotional appeal - “To be safe, please check now”: Here we have a repeat of the call to action, this time with an emotional appeal to the recipient's “safety,” which is a common tactic. Scammers will use emotional appeals and keyword triggers like “urgent” or “immediately.” All of these emotional trigger words should serve as a warning that you are being emotionally manipulated to take action that might be against your best interests.
- Hidden URL: This URL, as with others in the email, reveal a fraudulent URL when your cursor is hovering above it. This is a trick you can use for any link in any email; simply hover your cursor over the link without clicking, and preview the URL. If it doesn't match what the text of the URL says, or shows a clearly malicious URL hiding beneath the text, then don't click! The hidden URL in this case went to a fake landing page that was designed to harvest banking and credential information.
- Non-existent Office at TXST: The word “Bursar,” though a real word for a real job title, in the context of Texas State University, this doesn't make any sense. We don't have a Bursar's Office, and all financial aid issues go through the Financial Aid Office.
Responding to Phishing
Phishers are improving all the time, which makes it ever-more important to know how to spot and respond to phishing before you catch a hook. Correctly responding to a phishing email, voicemail, or text means being critical, observant, and restrained. To avoid becoming a victim one must be able to analyze the source and content of an email or message, observe what emotional triggers are being pulled, and refrain from clicking on suspicious links, downloading unknown content, or giving over sensitive and personal information to malicious actors.
Some basic best practices can help you avoid becoming a victim:
- Know who is contacting you - Phishers and scammers rely on both our natural inclination to help people and our emotional responses to stimuli in order to manipulate our behavior. One of the ways they do this successfully is to impersonate someone known and trusted in order to bypass our subconscious defenses; this could be a person of authority, a coworker, or even a relative. They will often spoof an email address or cell phone number in order to appear legitimate. Knowing what people’s correct contact information is can be vital in catching a phish. If you suspect someone is trying to phish you, try to reach out to the supposed sender on a known secure channel (usually a phone call) and just ask them if they sent the suspicious email or the text.
- Do not be reactive - A favorite tactic amongst cyber criminals is to push you to act fast by either incentivizing or threatening you. Some of them will tell you that you have only a few minutes to respond, implying there is ransomware on your machine or that they have compromising information on you that they will spread to your friends and family. Other times, they will tell you that your account will be suspended unless you update your personal details immediately. When you come across these kinds of emails, it’s best to just ignore them. Most reliable organizations give ample time before they terminate an account and they never ask patrons to update personal details over the Internet. When in doubt, visit the source directly rather than clicking a link in an email.
- If it's too good to be true, it probably is - Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately. For instance, many claim that you have won an iPhone, a lottery, or some other lavish prize. There might be a job offer that pays more than it should and implies that the work will be easy and fast. Don’t click on links in suspicious emails and don’t reply to unknown senders, especially if they try to solicit personally identifying information, like your banking information, address, or social security number from you over the Internet. Remember that if it seems to good to be true, it probably is!
- Inspect all Hyperlinks - A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different or it could be a popular website with a misspelling, for instance www.bankofarnerica.com – the ‘m’ is actually an ‘r’ and an ‘n’, so look carefully. Scammers and phishers will often use look-a-like URLs to try and fool you into believing a link is real.
- Avoid attachments - If you see an attachment in an email you weren’t expecting or that doesn’t make sense, don’t open it! They often contain payloads like ransomware or other viruses.
More Tips to Avoid Getting Hooked by a Phish
- No reputable organization will ever ask you for confidential information via e-mail.
- Never respond to an e-mail from a source you are not 100 percent sure of; when in doubt, call them.
- Never be afraid to call the company. If they want your information, they should be able to take it over the phone. Even if you do call a company, it doesn’t hurt to ask why they need to collect certain information.
- Always check the authenticity of a Web site before you provide any of your personal information.
- Never click on a link in a suspicious e-mail because it may take you to a malicious site. Open a new browser window and navigate to the page yourself.
- Phishing e-mails may contain strange words, misspelled words or unusual or awkward phrasing to help them avoid SPAM-filtering software.
- Don’t take good grammar as a sure sign of authenticity.
- Phishers are getting smarter, and oftentimes copy legitimate messages. Be sure to look for other suspicious markers.
Reporting Phishing
Outlook for Windows and Office 365
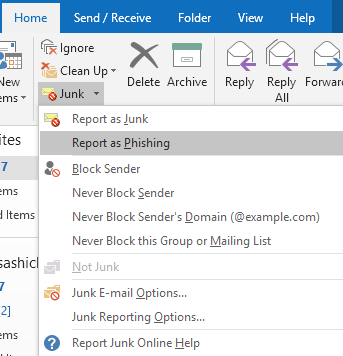
Select Junk from the Home ribbon.
Then select Report as Phishing as shown in the screenshot.
Once you select Report as Phishing, Outlook will prompt you to finalize the report.
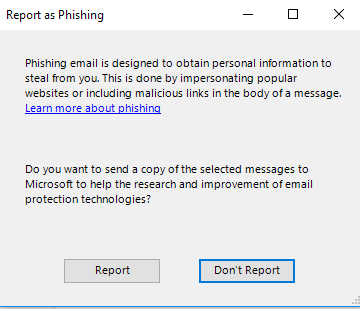
Click Report to send the email to Information Security.
To ensure you do not accidentally follow any links within the email, proceed to delete it from your Inbox and Deleted Items folders.
NOTE: If you click Don't Report the message will move to your Junk Email.
O365 Web Portal
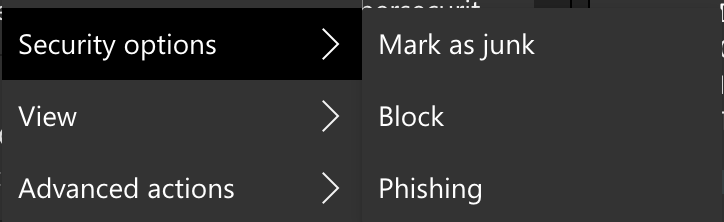
In the web portal, right click on the email to report.
Hover over "Security Options" and then select "Phishing"
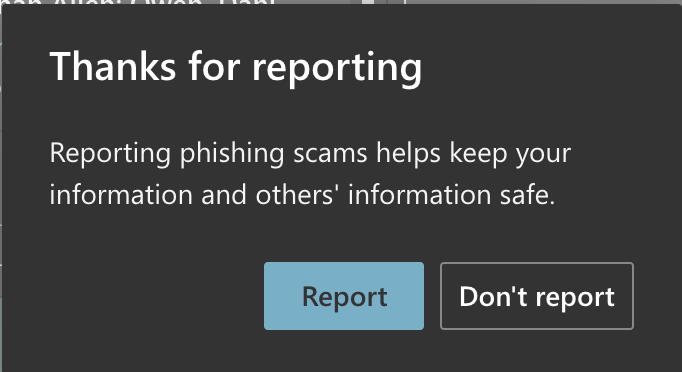
Click Report to send the email to Information Security.
To ensure you do not accidentally follow any links within the email, proceed to delete it from your Inbox and Deleted Items folders.
NOTE: If you click Don't Report the message will move to your Junk Email.
Microsoft Outlook for Mac
- Select the message
- Right-click on the message, and choose “Forward as Attachment.”
- Send that message to abuse@txstate.edu