Data Classification
-
Data Classification Guide
Texas State University uses a TXST uses a 3-tier data classification scheme established by UPPS 04.01.11 § 02.08 a, b, c. The table below provides a quick reference chart for institutional data classification. Please visit https://infosecurity.txst.edu/work/law-policy/policy-university.html to learn more.
Confidential Information Sensitive Information Public Information Level of Sensitivity High Moderate Low Legal Requirements Protection of data is required by law (e.g., TPIA, FERPA, and HIPAA data) or contractual agreements. Often considered “public” in the sense it is releasable under the Texas Public Information Act, some assurance is required so release of information is both controlled and lawful. Public information by its very nature is designed to be shared broadly, without restriction, at the complete discretion of the owner. Disclosure Risk Confidential information presents the most serious risk of harm if improperly disclosed. Unauthorized disclosure of Sensitive information could adversely impact the University, individuals or affiliates. Confidential information presents the most serious risk of harm if improperly disclosed. Examples of Information • Social Security numbers
• Credit card info
• Personal health info
• Student records
• Crime victim info
• Library transactions
• Court sealed records
• Access control credentials• Performance appraisals
• Employee DOB
• Employee email addresses
• Donor information
• Voicemail records
• Email contents
• Unpublished research•Job posting
• Service offerings
• Published research
• Directory information
• Degree programs
• General information about university products and services
-
Public Data
This system was determined to have a data classification of public. Therefore, this information system must not store, process, and/or transmit any sensitive or confidential information.
-
Sensitive Data
This system was determined to have a data classification of sensitive. Therefore, this information system must not store, process, and/or transmit any confidential information (e.g., grades, medical information, payment-card information, identifiable dates of birth). This information system must only store, process, and/or transmit the minimum-viable amount of sensitive information as required in order to function.
- To the greatest extent practicable, data elements with a reduced data classification should be used in lieu of data elements with higher data classification whenever possible (e.g., anonymizing records where feasible, using a Texas State email address or NetID instead of a personal phone number).
- Standards for Sensitive and Confidential Information outlines the methods by which this data is transferred, stored, processed, and otherwise handled
-
Confidential Data
This system was determined to have a data classification of confidential. Therefore, this information system must only store, process, and/or transmit the minimum-viable amount of sensitive and/or confidential information as required in order to function.
- To the greatest extent practicable, data elements with a reduced data classification should be used in lieu of data elements with higher data classification whenever possible (e.g., anonymizing records where feasible, using a Texas State email address or NetID instead of a personal phone number or social security number or individual taxpayer identification number).
- Standards for Sensitive and Confidential Information outlines the methods by which this data is transferred, stored, processed, and otherwise handled
System Categorization & Impact Designation
System categorization is somewhat similar to data classification. Relative to categorization, data classification is narrowly focused on confidentiality requirements of a specific set or type of information. In contrast, system categorization is broader and is based on the institutional impact of an incident that would affect the confidentiality, integrity, or availability of the information system or the university information it stores, processes, or transmits. More information on system categorization can be found here: https://infosecurity.txst.edu/work/spg/standards-system-categorization.html
-
Impact Designation
- Impact values used to categorize an information system are different than those used to describe actual incidents as detailed in UPPS 04.01.11, Section 02.03. More granular impact values are used in system categorization in order to better inform institutional planning and risk management based on probable scenarios and applied safeguards.
- The institutional impact of a potential incident that could affect an information system and/or university information it stores, processes, and/or transmits shall be classified by one of five values. Care should be exercised to consider the institutional perspective rather than the effects on an individual team or user.
- The following table describes each of the five impact values used as part of system categorization.
Impact Value Impact Description Severe (5) - The effect will cause the university to not achieve its goals and initiatives;
- the effect will significantly harm a large amount of stakeholders or the institution;
- the effect will have direct, long-lasting effects to core infrastructure systems, services, or other high-value, business-critical information resources;
- the effect will negatively affect a significant amount of sensitive or confidential information;
- the effect will cause loss of life or endanger serious, life-threatening injuries;
- the effect will cause catastrophic financial harm; and/or
- it is an institutional showstopper.
Major (4) - The effect will cause the component not to achieve its goals and initiatives;
- the effect will significantly harm a moderate amount of stakeholders or will cause some harm to a large amount of stakeholders or the institution;
- the effect will degrade or have short-lived effects to core infrastructure systems, services, or other high-value, business-critical information resources;
- the effect will negatively affect a moderate amount of sensitive or confidential information;
- the effect will cause significant financial harm; and/or
- it is a showstopper.
Moderate (3) - The effect will cause the university or component to operate inefficiently or expend unplanned resources to meet goals and initiatives;
- the effect will cause insignificant harm to stakeholders or the institution;
- the effect will degrade or have short-lived effects to non-essential systems, services, or other information resources that are not business-critical;
- the effect will cause some financial harm; and/or
- the effect will negatively affect some amount of sensitive or confidential information.
Minor (2) - The effects should be monitored to determine if action is required;
- the effect will not cause any direct harm to stakeholders or the institution;
- the effect will temporarily degrade or have minor, short-lived effects to non-essential systems, services, or other information resources that are not business-critical;
- the effect will cause a minor amount of financial harm; and/or
- the effect will negatively affect some amount of non-confidential information.
Insignificant (1) - The measurable effect upon the achievement of university’s goals and initiatives would be immaterial or insignificant;
- the effect will not cause any harm to stakeholders or the institution;
- the effect will have no effect to other institutional systems; and/or
- the effect will negatively affect some amount of public information.
-
Assessing Impact
- Three separate impact values shall be determined for each information system based on the descriptions outlined in section 1.C above.
- Each impact value assesses the institutional impact of an incident affecting, respectively, the confidentiality, integrity, and availability of the system and/or the information it stores, processes, and/or transmits. The three impact values determined are:
- Impact value (Confidentiality): Assesses the institutional impact of an incident affecting system or information confidentiality. Examples of incidents affecting confidentiality include, but are not limited to, data breaches, leaks, sending information to incorrect recipients, theft or loss of storage media or hard copies, and granting a user an inappropriately high level of access to data.
- mpact value (Integrity): Assesses the institutional impact an of incident affecting system or information integrity. Examples of integrity incidents include, but are not limited to, data corruption in transmission or at rest and inappropriate or unintentional modification or deletion of data by authorized or unauthorized users.
- Impact value (Availability): Assesses the institutional impact an of incident affecting system or information availability. Examples of availability incidents include, but are not limited to, system outages or downtime and data or system loss or deletion.
- The highest of the three impact values for each information system will determine the category of the information system as noted in the below table:
Impact Value System Category Severe (5) Essential (V) Major (4) Critical (IV) Moderate (3) Moderate (III) Minor (2) Low (II) Insignificant (1) Insignificant (I) -
Translating Institutional System Categorization to Texas Government Code (TAC 202)
- Texas State uses a more granular, five-tiered system categorization scheme to better inform its risk management functions and other activities that may rely on such information. However, Texas Administrative Code, some information security frameworks, and other resources instead use a simpler, three-tier scheme for system categorization.
- The table below shows the translation of institutional system categories and TAC 202 Designations
Institutional System Category TAC 202 Designation Essential (V) High Impact Information Resource Critical (IV) Moderate (III) Moderate Impact Information Resource Low (II) Low Impact Information Resource Insignificant (I)
Texas Risk and Authorization Management Program (TX-RAMP)
-
What is TX-RAMP?
TX-RAMP stands for the Texas Risk and Authorization Management Program. It's a state-mandated program created to ensure that cloud computing services used by Texas government agencies, including public universities, meet minimum security requirements.
-
Key Points
Purpose:
To protect sensitive state and institutional data when using cloud services.Scope:
Applies to cloud-based systems (like SaaS, PaaS, IaaS) used by state entities.Certification Levels:
Cloud providers that fall within scope of TX-RAMP must be certified at one of two levels:- TX-RAMP Level 1: For systems that are low-impact and handling confidential data.
- TX-RAMP Level 2: For systems that are moderate/high-impact
More information on system categorization can be found here: https://infosecurity.txst.edu/work/spg/standards-system-categorization.html
Requirement:
Agencies must not acquire or use cloud services that fall under TX-RAMP unless the service is certified at the appropriate level.Enforcement:
Non-compliant cloud services can’t be purchased or renewed. In some cases, current usage may be revoked—even if a contract is still active.
Accounts, Authentication, and Permissions
-
SSO Supported
SAML2-based Single Sign-On (SSO) must be used to authenticate all users to this information system. --Access to the information system must be promptly revoked when a user loses the need to access the information system (e.g., employee separation, changes in job duties)
-
Individual Account Creation - SSO and MFA not supported
This information system does not support Single Sign-On (SSO), and instead, individual accounts must be created and managed within the information system in a manner compliant with the university’s Standards for Identification and Authentication (seehttps://infosecurity.txst.edu/work/spg/standards-identity-authentication.html). Requirements of the standard include:
- Unique accounts must be created for each individual user within the information system.
- Passwords for those accounts must be stored in each user’s TXST LastPass Enterprise password vault.
- Passwords for each account must be:
- Unique (i.e., not users’ NetID passwords or derivative of other passwords);
- Randomly generated via LastPass Enterprise;
- Composed of as many character types as the service supports (i.e. upper-case letters, lower-case letters, numbers, and symbols);
- Set to at least 15 characters in length; and
- Changed annually.
- The ISO must be contacted if or when SSO becomes available for this information system to determine if SSO option(s) available are compatible with the university’s SSO services prior to enablement of the feature.
-
Individual Account Creation - Only MFA is supported
This information system does not support Single Sign-On (SSO), and instead, individual accounts must be created and managed within the information system in a manner compliant with the university’s Standards for Identification and Authentication (seehttps://infosecurity.txst.edu/work/spg/standards-identity-authentication.html). Requirements of the standard include:
- Unique accounts must be created for each individual user within the information system.
- Passwords for those accounts must be stored in each user’s TXST LastPass Enterprise password vault.
- Passwords for each account must be:
- Unique (i.e., not users’ NetID passwords or derivative of other passwords);
- Randomly generated via LastPass Enterprise;
- Composed of as many character types as the service supports (i.e. upper-case letters, lower-case letters, numbers, and symbols);
- Set to at least 15 characters in length; and
- Changed annually.
- Multi-factor authentication (MFA) must be enabled for each user account. If MFA cannot be enforced through technical means (e.g., default settings for all users), user onboarding procedures and guidance implemented by the information resource owner and custodian must incorporate MFA enablement.
- The ISO must be contacted if or when SSO becomes available for this information system to determine if SSO option(s) available are compatible with the university’s SSO services prior to enablement of the feature.
-
Access via a Shared Account
This information system is intended to be accessed through the use of a single account shared between multiple individuals. The information resource owner and custodian understand and accept the risks associated with this method of access (e.g., little to no individual accountability of users, diminished ability to attribute actions within the system to individual users, increased risks of account compromise because of incompatibility with multi-factor authentication). This shared account must be used and managed in a manner compliant with the university’s Standards for Identification and Authentication (see https://infosecurity.txst.edu/work/spg/standards-identity-authentication.html). Requirements of the standard include the following:
- The shared account must be tied to a limited access, shared @txstate.edu email address (i.e., a shared mailbox or a distribution list). Note, shared mailboxes and distribution lists may be requested via the IT Assistance Center’s website.
- The password for the shared account must be stored in the information resource owner’s TXST LastPass Enterprise password vault.
- The password for the shared account must be:
- Unique (i.e., not users’ NetID passwords or derivative of other passwords);
- Randomly generated via LastPass Enterprise;
- Composed of as many character types as the service supports (i.e. upper-case letters, lower-case letters, numbers, and symbols);
- Set to at least 15 characters in length; and
- Changed annually.
- The password may only be shared via LastPass Enterprise with authorized users.
- Any time an authorized user loses their need to access the password (e.g., employee separation or change in job duties), that user’s access to the password must be promptly revoked via LastPass, and the password must then be changed.
- The list of users with access to the password in LastPass Enterprise must be reviewed at least twice a year or at the end of each long semester to ensure only authorized users have access to the shared credentials. If unauthorized users are discovered to have access to the credentials, their access must be removed, and the password must be reset.
-
Apple/iCloud Accounts
- Apps must be purchased in collaboration with IT Business Services and tied to Apple accounts created with @txstate.edu addresses.
- Unless otherwise authorized, apps should not be purchased using personal credit cards or gift cards.
- Unless otherwise authorized, apps should be purchased and deployed in a manner that allows the apps to be reclaimed following the conclusion of their use by an individual (i.e. allowing Texas State to retain ownership of that license following the separation of an individual employee). When authorized, licenses purchased with the intent to be treated as consumable assets (e.g. vouchers provided to students in a classroom setting).
- Unless otherwise authorized, apps should be installed on university-owned devices instead of personally owned equipment.
- University-owned devices must be managed in a fashion commensurate to the use case and data they will handle; these recommendations may be provided separately from this set of guidelines.
Owner and Custodian Responsibilities
-
Accounts, Authentication, and Permissions
- Access to the information system must be promptly revoked when a user loses the need to access the information system (e.g., employee separation, changes in job duties).
- Users and administrators within this information system must only be granted the minimum-viable set of permissions required and approved by the information resource owner (i.e., in alignment with the model of least privilege).
- User accounts and permissions must be reviewed by the information resource owner and custodian at least twice a year or at the end of each long semester to ensure, at minimum, (a) only users with a need to access the system have active accounts and (b) active user accounts only have the minimum-viable set of permissions required and approved by the information resource owner.
-
Data Storage, Processing, and Transmission
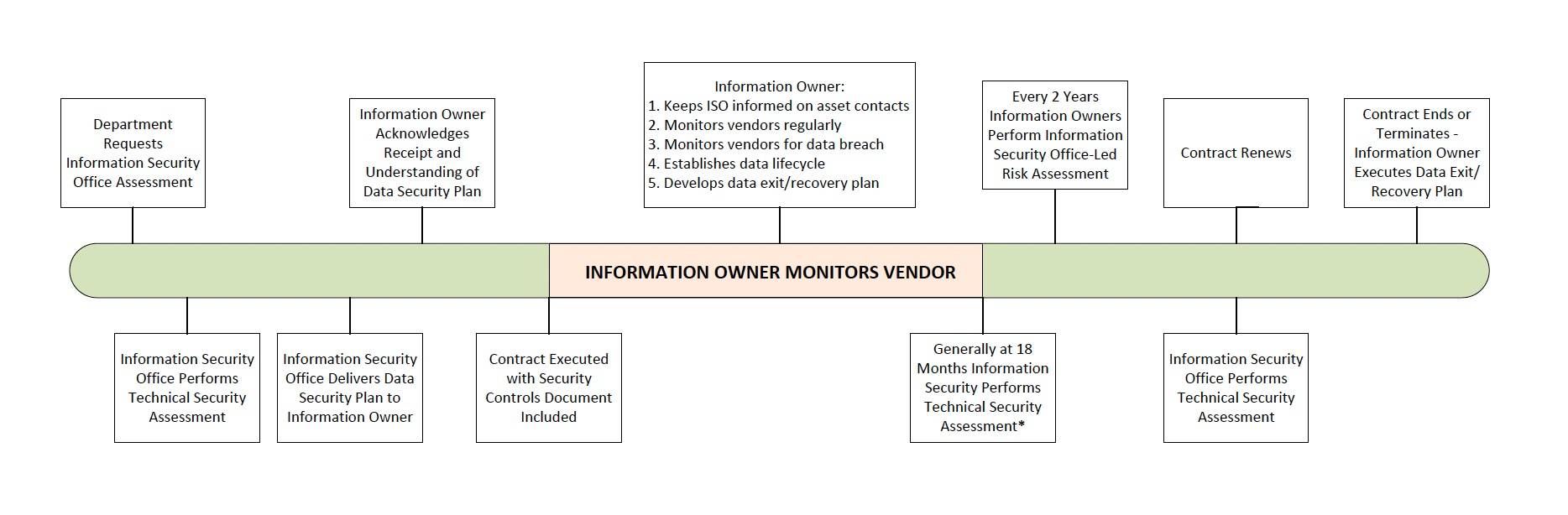
A data lifecycle for information stored, processed, and/or transmitted by this information system must be established and maintained by the Information Resource Owner and Custodian in order to remove information that no longer needs to be retained in the system while also remaining compliant with the University Records Retention Schedule (see: https://www.univarchives.txst.edu/records/rm-rrs.html for more information).
-
Configuration
- Authentication and access management controls must be configured, enabled, and tested by the information resource custodian and/or owner prior to the use of this information system for production purposes or to store, process, or transmit any production or non-public information.
- Unless separately assessed and authorized by the ISO, features that were not included in this assessment are outside the scope authorization and may not be used or enabled unless or until separately assessed and authorized.
-
Data Recovery or Exit Plan
A data recovery or exit plan must be established by the Information Resource Owner and Custodian in order to prepare for the possibility of termination of the use of this information system (e.g., determining what data would need to be retrieved and preserved, confirming the means by which information may be exported). Such planning will be important to the continuity of operations and compliance with applicable record retention requirements if or when the information system is replaced and/or decommissioned.
-
Biometric or GPS-based Location Information
If individually identifiable biometric or GPS-based location information will be stored, processed, and/or transmitted by tine information system or related information system components, the institution’s Data Management Officer must be contacted to consult on data-subject consent management processes as required by Texas Government Code and University policy.
-
Risk Assessments
The Information Resource Owner and Information Resource Custodian will be responsible to conduct a biennial, ISO-led risk assessment of this service. They will receive notification and assistance from the ISO when the risk assessment period for this information system begins.
-
Breach Notifications
The Information Resource Owner and Custodian must promptly inform the ISO of any actual or suspected data breaches, misuse or abuse, or other security incidents related to the information system.
Integrations with Other Information Systems
-
Integration Controls
- Unless otherwise assessed and authorized by the ISO, no integration between this information system and other products, systems, services, or platforms may be established or used. This includes university-managed information systems as well as external services and information systems that are otherwise unauthorized or have not yet been assessed.
- For clarity, the use of endpoint devices like university-owned computers to access or use the information system is generally expected and authorized. Similarly, if Single Sign-On (SSO) is available as a means of authentication, connections with the planned SSO service is also expected and authorized.
- Features or interconnections that may involve payment-card data or processing of payment cards must be authorized by the Office of the Treasurer and/or Student Business Services.
- For clarity, authorization by the Office of the Treasurer and/or Student Business Services is not required if the extent to which payment-card data will be involved is limited to the use of a university procurement card (i.e., "P-Card") to purchase access to or licensees for this information system.
- Unless otherwise assessed and authorized by the ISO, no integration between this information system and other products, systems, services, or platforms may be established or used. This includes university-managed information systems as well as external services and information systems that are otherwise unauthorized or have not yet been assessed.
Systems Hosted On-Premises
-
Information System is intended to be accessed directly from the internet
This information system will be intended to be accessed directly from the Internet. After the information system has been configured but prior to production use or the introduction of non-public or production data, the information system must be subjected to an ISO-led vulnerability scan, and any subsequent findings must be resolved. Following the resolution of identified vulnerabilities, a network firewall exception request form may then be submitted.
- Vulnerability scans may be requested using the following form on the ISO’s website: https://infosecurity.txst.edu/services-tools/security-services/vulnerability-scan.html
- Network firewall exceptions may be requested using the following form on the ISO’s website: https://infosecurity.txst.edu/services-tools/security-services/firewall-exception.html
-
Information System will not be accessed directly from the internet
This information system will not be intended to be accessed directly from the Internet. After the information system has been configured but prior to production use or the introduction of non-public or production data, the information system must be subjected to an ISO-led vulnerability scan, and any subsequent findings must be resolved.
- Vulnerability scans may be requested using the following form on the ISO’s website: https://infosecurity.txst.edu/services-tools/security-services/vulnerability-scan.html
-
Information System will reside in a restricted network
This information system and/or related information system components must reside in a restricted-access network that will be managed in collaboration between the ISO and Technology Resources’ Network Operations team.
Email Configuration Controls
-
Vendor will be sending email on behalf of TXST
A dedicated, fourth-level subdomain (e.g., noreply@updates.dept.txstate.edu) and a corresponding, narrowly scoped SPF/DKIM record should be used for sending email from this service provider.
- Third-level subdomains will require approval from the CISO and University Marketing (e.g., noreply@dept.txstate.edu).
- Subdomains can be requested here: https://gato.its.txst.edu/manage-website/url-request.html
- Reference: https://policies.txst.edu/university-policies/04-01-08.html
-
Email Marketing Vendors
Some email marketing vendors may provide additional services beyond email marketing such as SMS text messaging, two-way email communication through their platform, website hosting, and domain name registration. Unless otherwise vetted and authorized by the Information Security Office, these features are outside the scope of this data security plan and may not be used or enabled until otherwise vetted and authorized.
Risk Advisories
-
System is not compatible with SSO nor Multi-Factor Authentication
Upon review of the authentication options available for this information system, it was discovered that neither Single Sign-On (SSO) nor Multi-Factor Authentication (MFA) were supported. The lack of these features is counter to baseline requirements of university information systems and best practice. Without protection afforded by SSO or MFA, user accounts within this information system are at an elevated risk of compromise, which increases the likelihood of data breach or disclosure incidents, corruption or loss of data, and other negative outcomes. These risks must be accepted by at least the information resource owner and custodian before authorization may be granted by the ISO as an exception to the requirements of Standards for Identification and Authentication (IA-2).
-
System cannot be centrally managed/administered
Upon review, it was discovered that the information resource cannot be managed or administered via centralized systems used by the Division of IT to govern and protect the university’s devices (e.g., JAMF for macOS and iPadOS devices, SCCM for Windows devices). These systems allow the university to control its devices; monitor for malicious activity and applications; remotely wipe devices if they become lost, stolen, or compromised; ensure updates are installed; and prove ownership if the device is recovered after being lost or stolen.
-
Lack of attestation of penetration testing from vendor
Upon review of supporting documentation and with further consultation with vendor personnel, it was determined that pen-test results would not be made available. This is counter to baseline requirements for university information systems, as well as best practices. Without access to all required documentation, decisions regarding robust controls and configurations cannot be made. This condition creates an elevated risk of compromise, which increases the likelihood of an incident involving a data breach or disclosure, corruption or loss of data, and other negative outcomes. These risks must be accepted by at least the information resource owner and custodian before authorization can be granted by the ISO as an exception to the best practice standards.
-
Lack of governance and assurance that security controls are implemented
- Effective IT governance enables an organization to help establish and monitor accountability for IT activities to ensure that IT-enabled investments are aligned with enterprise objectives. Any misalignment can result in improper identification of critical services, along with substandard security controls. Additionally, impaired alignment between the enterprise and IT weakens communication and priorities, resulting in poor allocation of resources and a lack of transparency in actual risk reduction.
- TXST has established an IT governance framework that enables the effective management of IT risk and ensures that effective security controls are identified and implemented. TXST has no visibility into this system’s current IT governance and security control framework.
- The lack of an HECVAT or other security documentation has resulted in a diminished level of assurance that otherwise-standard objectives and security controls would be met.
-
No centralized monitoring for security incidents, abuse, or controls
- Upon review, it was determined that this service involves a third-party processing, storing or transmitting TXST data. The cloud infrastructure is completely owned, managed, and monitored by the service provider, so the cloud users have less control over the function and execution of services. One of the greatest challenges facing a cloud customer is the lack of an in-depth visibility needed to determine if data are adequately secured. Failing to maintain this visibility leaves TXST vulnerable to data exposure, unauthorized access, and other security threats.
- A cornerstone of any effective cloud-based system is how quickly threat notifications and alerts can be sent to website or security personnel. Unless a security alert or notification is issued by the provider, the customer won’t have the insight to recognize security incidents or other anomaly going wrong within the cloud infrastructure. This lack of information prevents the institution from being able to detect and respond to incidents prior to discovery by impacted user(s) or to engage in measures that would reduce the likelihood of an incident. Additionally, if an incident were to occur, such as a compromised account, Texas State would have no access to critical event logging information required for conducting a due diligence investigation.
-
Critical vulnerabilities found
Vulnerabilities classified as critical have been found by TXST's third party risk management partner in this system's cloud services. The ISO will provide detailed vulnerability information to the information system owner. Along with the Data Security Plan (DSP), a detailed list of findings will be sent to the Information System Owner and Custodian. The Information System Owner/Custodian should share this information with the vendor so they can determine how these vulnerabilities can be mitigated.
-
Recent data security breach
It has been determined that the vendor has recently been exposed to a data security breach. Using a vendor that has recently experienced a security breach presents a significant risk to TXST, including potential exposure of sensitive data, service disruptions, and non-compliance with regulatory requirements. The breach may indicate vulnerabilities in the vendor’s security controls, increasing the likelihood of future incidents. Without clear assurances of remediation efforts and improved security measures, continued reliance on the vendor could compromise data integrity, confidentiality, and overall cybersecurity posture. The Information Resource Owner agrees to implement and maintain appropriate safeguards in accordance with applicable laws, regulations, and organizational policies to mitigate such risks. This includes adhering to cybersecurity best practices, and promptly reporting any suspected or confirmed breaches.
-
System requires TX-RAMP compliance prior to implementation
The Information Security Office grants conditional authorization for this system. However, implementation of this solution is not authorized until the vendor has obtained the required TX-RAMP certification.
-
Vendor refused to sign the Information Security & Accessibility Standards Exhibit
It was determined that the vendor refused to sign a contract addendum that focuses on security posture and assurance that proper controls are implemented. Without this assurance and addendum, several significant risks arise for the TXST. These include:
1. Regulatory Non-Compliance
The addendum includes mandatory compliance with federal and state laws like FERPA, HIPAA, GLBA, TAC 206/213, and Section 2054.138 of the Texas Government Code. Refusal to sign could indicate the vendor is either unwilling or unable to meet these legal obligations, exposing the institution to regulatory violations and potential fines.
2. Data Security Risks
The addendum outlines strict requirements for data encryption (at rest and in transit), custodianship, audit logging, breach notification, and key management. A vendor that won’t agree to these standards poses a significant risk of data breach, unauthorized data access, or mishandling of sensitive institutional data.
3. Loss of Control Over Data
The institution's ownership and control over its data is a foundational term in the addendum. A vendor's refusal suggests the potential for disputes over data rights, limitations on data retrieval or deletion, and unclear responsibilities at the end of the contract term.
4. Inability to Enforce Remedies
The addendum provides clear remedies, including injunctive relief, for unauthorized disclosure or breach of contract. Without the vendor’s agreement, the institution may have limited legal recourse in the event of noncompliance or data misuse.
5. Lack of Transparency and Trust
A refusal may signal that the vendor’s internal security practices, documentation, or service architecture do not meet minimum standards—or that they are unwilling to allow transparency (e.g., audit logs, breach reporting, or security certifications).
6. Operational and Institutional Risk
Vendors not meeting these standards can jeopardize grant funding, academic partnerships, or federal contracts (especially under frameworks like CMMC, NIST 800-171, or similar), which often require secure handling of controlled or sensitive information.